Overview
Keys serve as the secure communication and information security, functioning as essential digital elements. Their critical role involves encrypting and decrypting data, confirming identities, and upholding the security triad of confidentiality, integrity, and authenticity for information.
There are different kinds of key, widely used to for encryption algorithm, for increasing the security efficiency of protecting data.
The Keys that are available in ezto auth are, aes-generated, ecdsa-generated, hmac-generated, java-keystore, rsa, rsa-enc, rsa-enc-generated, and rsa-generated.

aes-generated
The Advanced Encryption Standard (AES) is a highly symmetric encryption algorithm renowned for its security and efficient data protection capabilities. When data or content is designated as "AES-generated," it indicates that AES encryption or encryption-related methods have been employed to safeguard it.
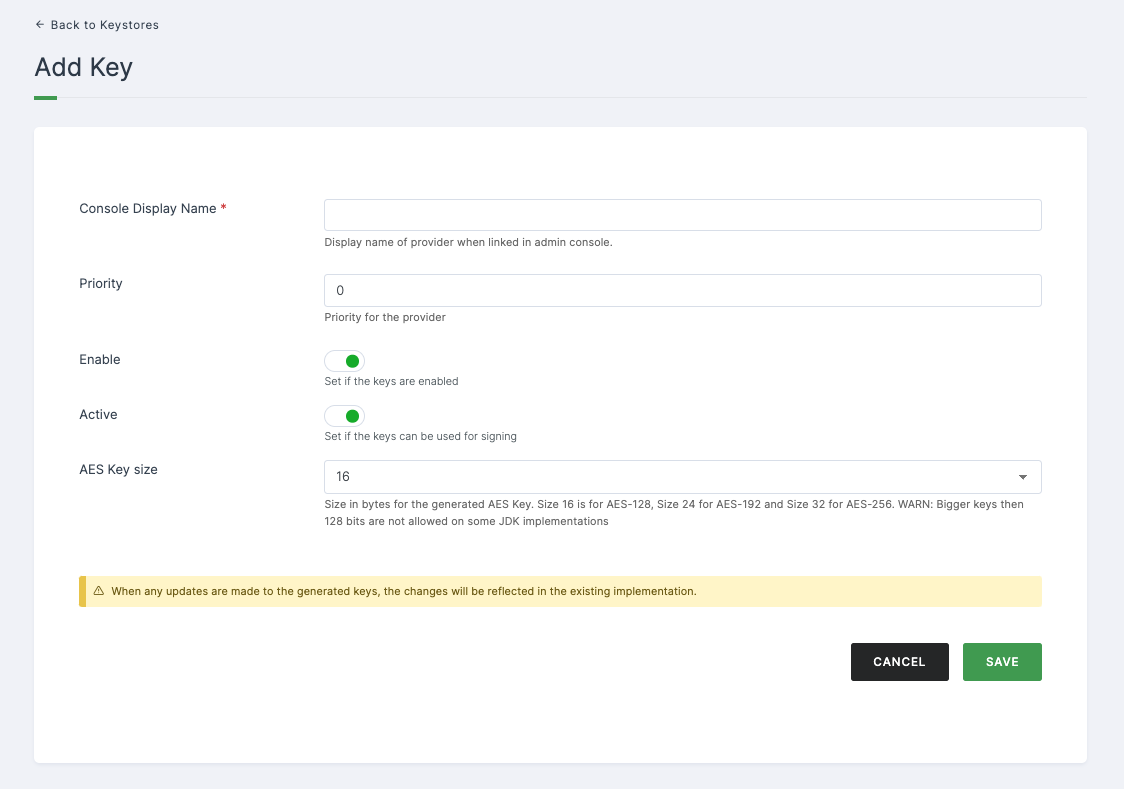
Configurations
| Configuration | Description |
|---|---|
| Console Display Name | This field represents the display name of the provider when linked in the admin console. |
| Priority | Priority level assigned to the provider. |
| Enable | Indicates whether the keys are enabled or not. |
| Active | Indicates whether the keys can be used for signing. |
| AES Key Size | This field specifies the size in bytes for the generated AES Key. A size of 16 corresponds to AES-128, a size of 24 corresponds to AES-192, and a size of 32 corresponds to AES-256. Note: Some JDK implementations may not allow keys larger than 128 bits; caution is advised. |
➤ After providing the necessary configurations > Click on SAVE
ecdsa-generated
It commonly denotes something that has been produced or formed through the utilization of the Elliptic Curve Digital Signature Algorithm (ECDSA). ECDSA is a widely adopted cryptographic technique employed for generating digital signatures and confirming their legitimacy. When data or content is labeled as ECDSA-generated, it signifies that the ECDSA algorithm has been utilized in its creation, frequently for tasks related to digital signatures and authentication.
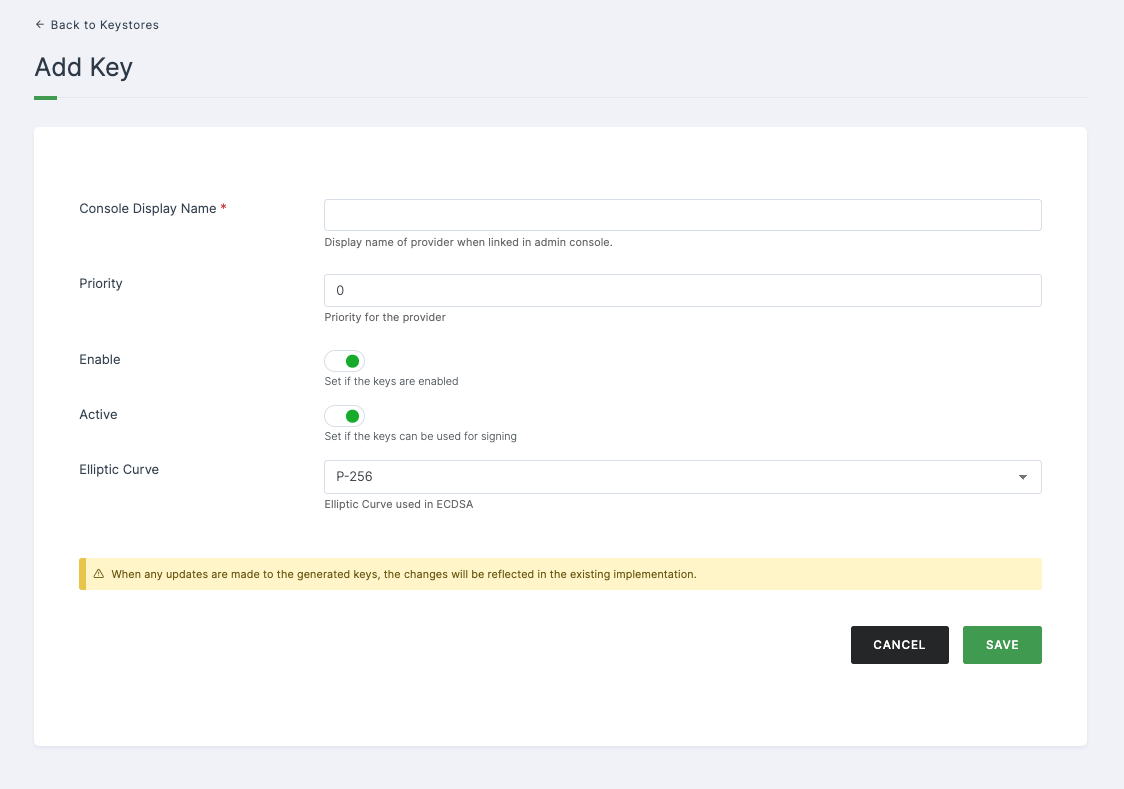
Configurations
| Configuration | description |
|---|---|
| Console Display Name | This field represents the display name of the provider when linked in the admin console. |
| Priority | Indicates the priority level assigned to the provider. |
| Enable | Specify whether the keys are enabled or not. |
| Active | Indicate whether the keys can be utilized for signing. |
| Elliptic Curve | The Elliptic Curve employed in ECDSA. |
➤ After providing the necessary configurations > Click on SAVE
hmac-generated
It generally denotes an entity or data that has been generated or formed using the Hash-based Message Authentication Code (HMAC) algorithm. This widely adopted cryptographic technique plays a key role in ensuring the integrity and authenticity of data by employing a shared secret key.
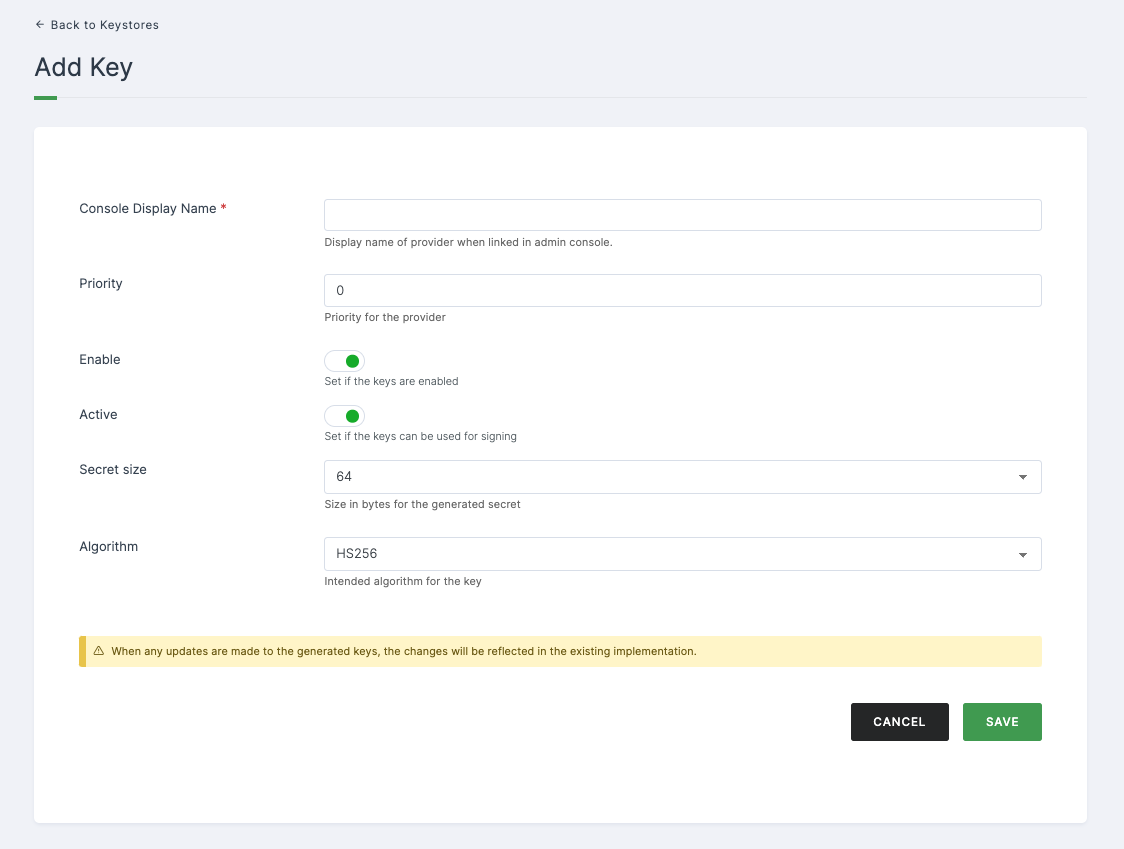
Configurations
| Configuration | description |
|---|---|
| Console Display Name | This field indicates the display name of the provider when linked in the admin console. |
| Priority | Denotes the priority level assigned to the provider. |
| Enable | Specifies whether the keys are enabled or not. |
| Secret Size | The size in bytes for the generated secret. |
| Algorithm | The intended algorithm for the key. |
➤ After providing the necessary configurations > Click on SAVE
java-keystore
A java keyStore, commonly known as "JKS," serves as a storage facility for cryptographic keys, certificates, and other confidential security-related information. It forms an integral part of Java's security framework, finding extensive applications in securing communication, authenticating users and systems, and maintaining data integrity.
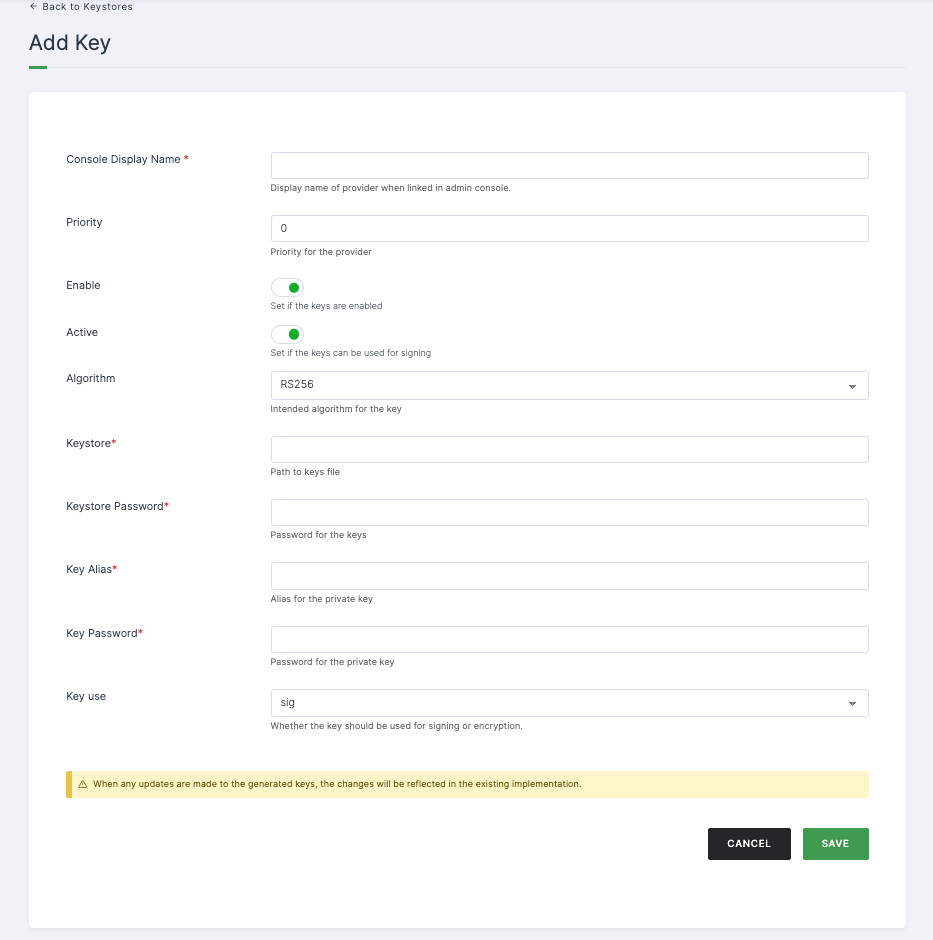
Configurations
| Configuration | description |
|---|---|
| Console Display Name | This field represents the display name of the provider when linked in the admin console. |
| Priority | Indicates the priority level assigned to the provider. |
| Enable | Specify whether the keys are enabled or not. |
| Algorithm | Denotes the intended algorithm for the key. |
| Keystore* | Path to the keys file. |
| Keystore Password* | Password for accessing the keys. |
| Key Alias* | Alias for the private key. |
| Key Password* | Password for the private key. |
| Key Use | Specifies whether the key should be used for signing or encryption. |
➤ After providing the necessary configurations > Click on SAVE
rsa
RSA, stands as a prominent public-key encryption and digital signature algorithm within the realm of cryptography. RSA persists as an integral cornerstone of contemporary secure communication and information security solutions.
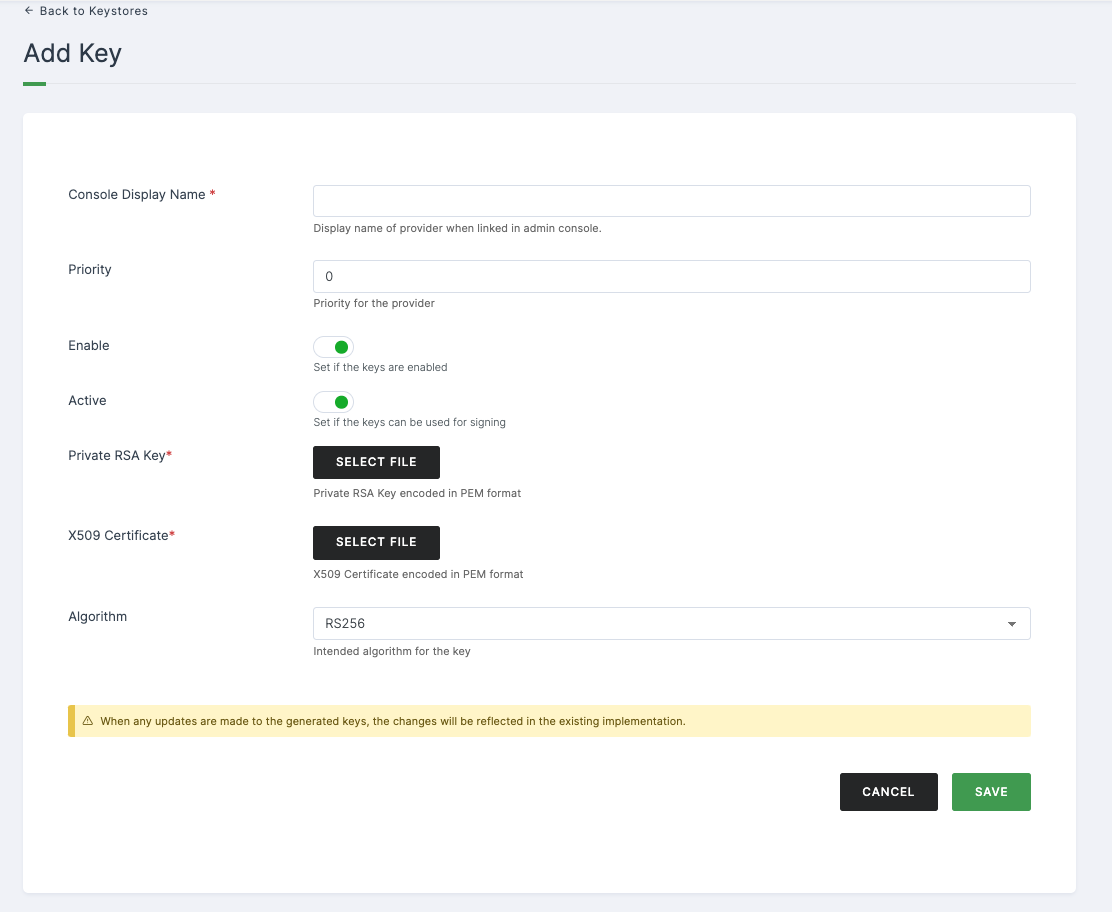
Configurations
| Configuration | description |
|---|---|
| Console Display Name | This field represents the display name of the provider when linked in the admin console. |
| Priority | Indicates the priority level assigned to the provider. |
| Enable | Specify whether the keys are enabled or not. |
| Active | Specify whether the keys can be used for signing. |
| Private RSA Key | The Private RSA Key encoded in PEM format. |
| X509 Certificate* | The X509 Certificate encoded in PEM format. |
| Algorithm | Denotes the intended algorithm for the key. |
➤ After providing the necessary configurations > Click on SAVE
rsa-enc
It commonly denotes RSA encryption, a cryptographic technique that employs the RSA algorithm to safeguard data by transforming it into an indecipherable format, only accessible with the corresponding private key.
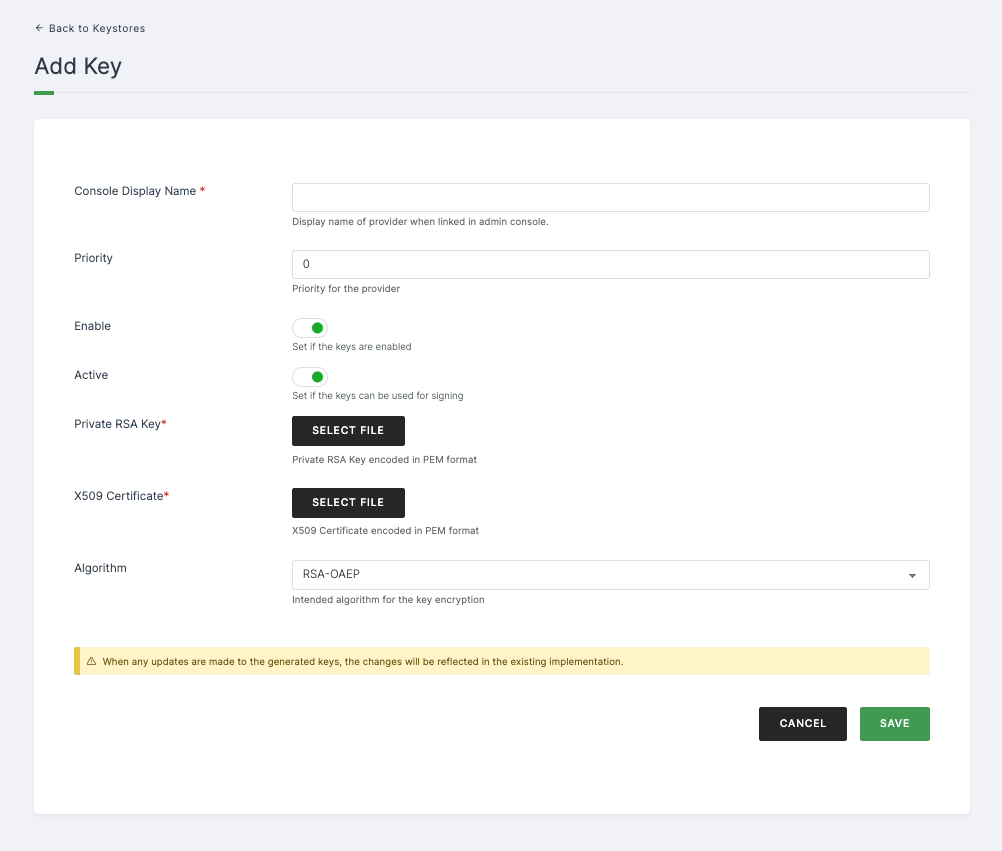
Configurations
| Configuration | description |
|---|---|
| Console Display Name | This field represents the display name of the provider when linked in the admin console. |
| Priority | Indicates the priority level assigned to the provider. |
| Enable | Specify whether the keys are enabled or not. |
| Active | Specify whether the keys can be used for signing. |
| Private RSA Key | The Private RSA Key encoded in PEM format. |
| X509 Certificate* | The X509 Certificate encoded in PEM format. |
| Algorithm | Denotes the intended algorithm for the key. |
➤ After providing the necessary configurations > Click on SAVE
rsa-enc-generated
It generally describes an entity or data that has been generated or produced using RSA encryption. RSA encryption relies on the RSA algorithm to protect data by transforming it into an unreadable format, that can only be deciphered using the matching private key.
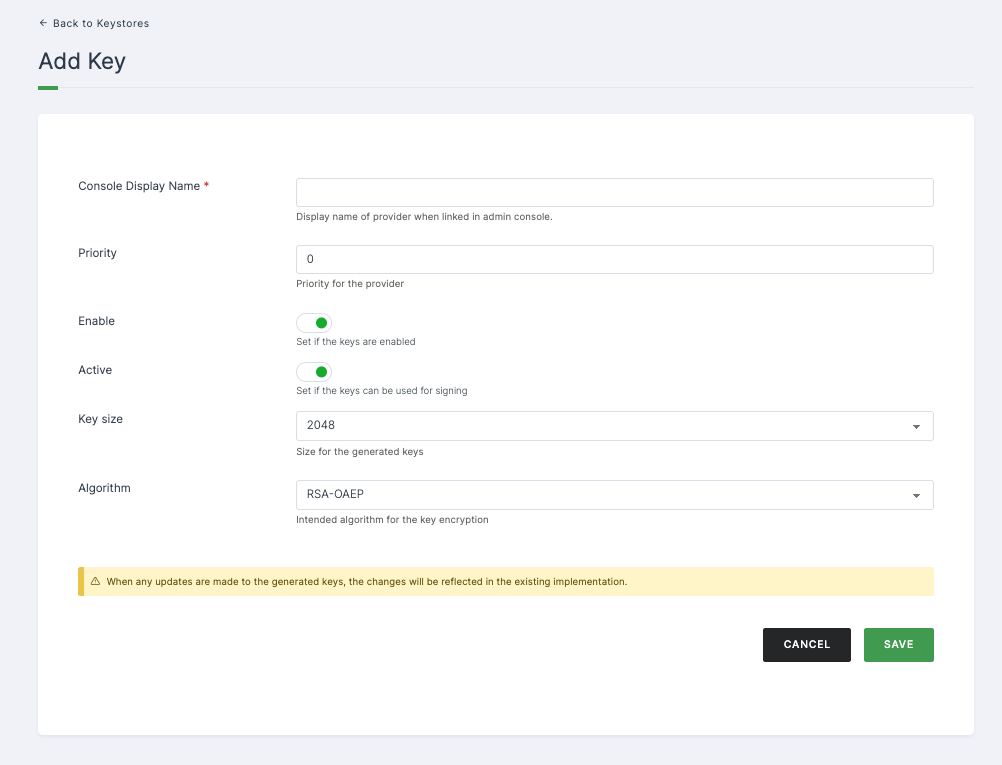
Configurations
| Configuration | description |
|---|---|
| Console Display Name | This field represents the display name of the provider when linked in the admin console. |
| Priority | Indicates the priority level assigned to the provider. |
| Enable | Specify whether the keys are enabled or not. |
| Active | Specify whether the keys can be used for signing. |
| Key Size | The size in bytes for the generated secret. |
| Algorithm | Denotes the intended algorithm for the key. |
➤ After providing the necessary configurations > Click on SAVE
rsa-generated
It generally refers to something that has been produced or created using the RSA encryption algorithm. RSA encryption employs mathematical techniques to secure data by converting it into an encrypted format that can only be deciphered with the associated private key.
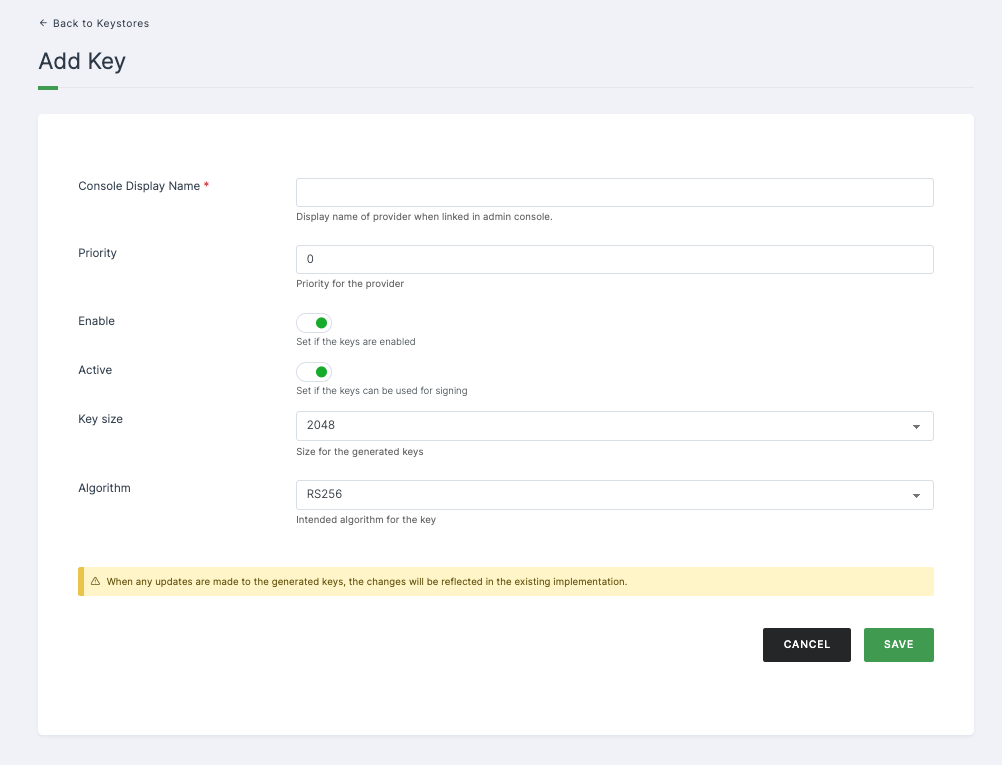
Configurations
| Configuration | description |
|---|---|
| Console Display Name | This field specifies the display name of the provider when linked in the admin console. |
| Priority | Indicates the priority assigned to the provider. |
| Enable | Set this option to determine if the keys are enabled. |
| Active | Set this option to determine if the keys can be used for signing. |
| Key Size | Indicates the size in bytes of the generated secret. |
| Algorithm | Denotes the intended algorithm for the key. |
➤ After providing the necessary configurations > Click on SAVE